Connecting the DotsTracking Two Identified Terroristsby Valdis KrebsSocial Network Analysis [SNA] is a mathematical method for 'connecting the dots'. SNA allows us to map and measure complex, and sometimes covert, human groups and organizations. Early in 2000, the CIA was informed of two terrorist suspects linked to al-Qaeda. Nawaf Alhazmi and Khalid Almihdhar
were photographed attending a meeting of known terrorists in Malaysia.
After the meeting they returned to Los Angeles, where they had already
set up residence in late 1999.  What do you do with these suspects? Arrest or deport them immediately? No, we need to use them to discover more of the al-Qaeda network. Once suspects have been discovered, we can use their daily activities to uncloak their network. Just like they used our technology against us, we can use their planning process against them. Watch them, and listen to their conversations to see...
The structure of their extended network begins to emerge as data is discovered via surveillance. A suspect being monitored may have many contacts -- both accidental and intentional. We must always be wary of 'guilt by association'. Accidental contacts, like the mail delivery person, the grocery store clerk, and neighbor may not be viewed with investigative interest. Intentional contacts are like the late afternoon visitor, whose car license plate is traced back to a rental company at the airport, where we discover he arrived from Toronto (got to notify the Canadians) and his name matches a cell phone number (with a Buffalo, NY area code) that our suspect calls regularly. This intentional contact is added to our map and we start tracking his interactions -- where do they lead? As data comes in, a picture of the terrorist organization slowly comes into focus. How do investigators know whether they are on to something big? Often they don't. Yet in this case there was another strong clue that Alhazmi and Almihdhar were up to no good -- the attack on the USS Cole in October of 2000. One of the chief suspects in the Cole bombing [Khallad] was also present [along with Alhazmi and Almihdhar] at the terrorist meeting in Malaysia in January 2000. 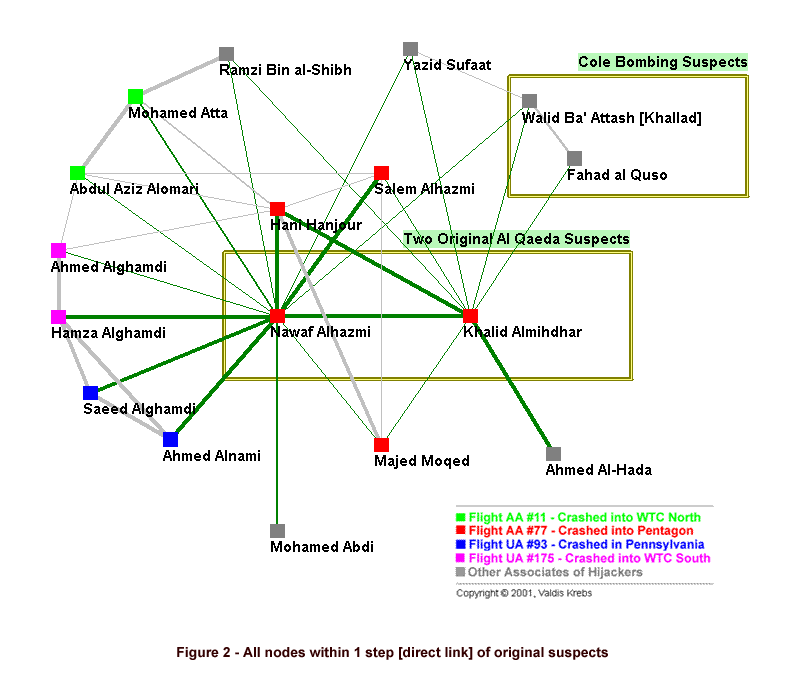 Figure 2 shows the two suspects and their immediate ties. All direct ties of these two hijackers are colored green, and link thickness indicates the strength of connection. Once we have their direct links, the next step is to find their indirect ties -- the 'connections of their connections'. Discovering the nodes and links within two steps of the suspects usually starts to reveal much about their network. Key individuals in the local network begin to stand out. In viewing the network map in Figure 2, most of us will focus on Mohammed Atta because we now know his history. The investigator uncloaking this network would not be aware of Atta's eventual importance. At this point he is just another node to be investigated. 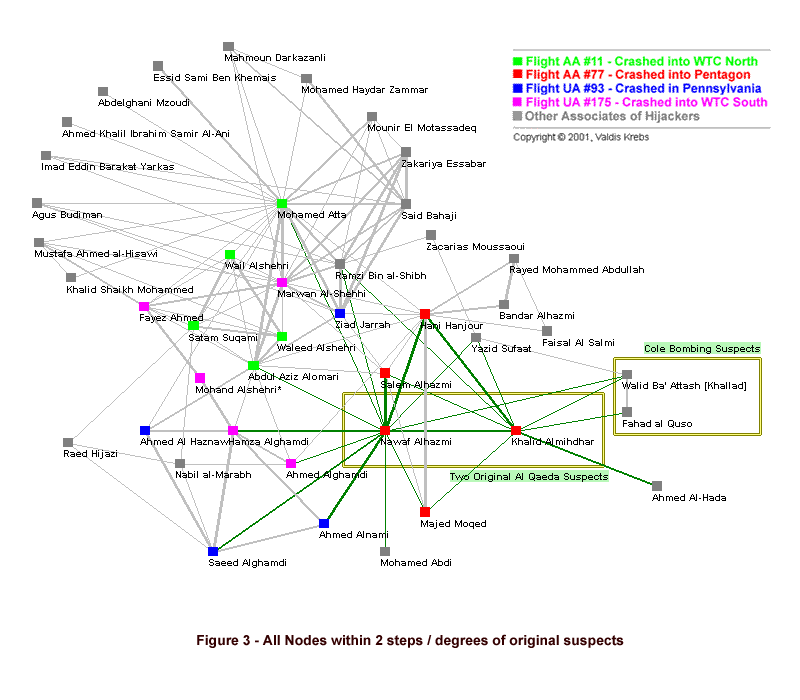 Figure 3 shows the direct connections of the original suspects as green links, and their indirect connections as grey links. We now have enough data for two key conclusions:
With hindsight, we have now mapped enough of the 9-11 conspiracy to stop it. Again, the investigators are never sure they have uncovered enough information while they are in the process of uncloaking the covert organization. They also have to contend with superfluous data. This data was gathered after the event, so the investigators knew exactly what to look for. Before an event it is not so easy. As the network structure emerges, a key dynamic that needs to be closely monitored is the activity within the network. Network activity spikes when a planned event approaches. Is there an increase of flow across known links? Are new links rapidly emerging between known nodes? Are money flows suddenly going in the opposite direction? When activity reaches a certain pattern and threshold, it is time to stop monitoring the network, and time to start removing nodes. IMHO this bottom-up approach of uncloaking a network is more effective than a top down search for the terrorist needle in the public haystack -- and it is less invasive of the general population, resulting in far fewer "false positives". All data for this analysis is 'open source' and was gathered from public sources on the WWW in late 2001 and early 2002. A more complete network map of the hijackers and reported others is available. I want to thank all those who provided constructive feedback on earlier versions of this document. This white paper was written under the assumption that all surveillance data is gathered via legal means and that it will stand up in a court of law. Update 2005In August 2005, U.S. Congressman Curt Weldon revealed a similar network map of 9-11-2001 terrorists that was created in 2000, also from open source information. The "Able Danger" secret US intelligence unit supposedly created that network maps. This project remained controversial throughout 2005. Here is an overview of "Able Danger" -- including blurred pictures of Able Danger maps. In December 2005, U.S. President George W. Bush revealed that he authorized the National Security Agency [NSA] to monitor phone calls and Internet traffic of US-based people with "terrorist links". My guess is that once the NSA gathers the data, it is assembled and analyzed in a fashion very similar to the above scenario. Update 2006It appears that the Canadian terror cell that was arrested in June 2006 was tracked and unraveled in method very similar to what I describe above. The Toronto Star reported that initially the suspects were spotted on web sites spewing anti-Western sentiments and the desire to attack in North America. This gave the Canadian intelligence community an entry point into the network. Then, starting at this entry point, they were able to discover others in the network using normal surveillance methods and linking them together. The Baltimore Sun reported that the surveillance received prior approval:
Canadian officials had to obtain permission from a threat-review committee before investigating Canadian citizens, he said. As a result, he said, all the information collected should be usable in court." In August 2006, a large terror plot -- to blow up U.S. passenger planes crossing the Atlantic Ocean -- was disrupted in England. The Scotsman reports the following:
In the initial stages, counter-terrorism officers watched from a distance. By sifting telephone records, e-mails and bank records, the MI5 officers built up what insiders call "concentric circles" of information, gradually connecting each suspect to others and building up a detailed picture of the conspiracy. Concentric circles of 1 and 2 steps? Looks like they followed the recipe above. It appears that this terror network was not disrupted by data mining of massive phone & financial records -- Big Brother was not involved. An entry point was found into the network, allowing the activity of the network to reveal the structure of the network -- all without bothering the other 60,000,000+ UK residents. Update 2007Jeff Jonas -- the genius behind NORA [Non-Obvious Relationship Awareness] -- comments on the congressional debate on data mining of massive phone-call data:
Home | Software | Training | Consulting | Case Studies | Blog | Contact |